What is threat detection?
Threat detection is a process which analyzes your cloud security stack to identify and flag any suspicious activity that could compromise your infrastructure. And once you get alerted of a probable threat, you can then identify what remediation steps can be implemented to neutralize the threat before it can exploit any present vulnerabilities.
Prevention, Detection, and Remediation: When hackers do successfully get into your system, you should be able to detect their presence quickly in order to minimize the damage. Adversaries have honed their skills during the pandemic, finding a gold mine of opportunities to hack organizations and steal sensitive data. With attacks growing in number and sophistication, organizations are struggling to keep pace. Companies must assume that an attack will eventually succeed. The ability to detect and respond to cyber attacks must therefore be expanded.
Threat Detection & MITRE ATT&CK Framework
The MITRE ATT&CK Framework is a well-documented knowledge base of Tactics, Techniques, and Procedures (TTPs). TTPs are patterns of behavior that real world actors employ. An example of this would be the https://www.fireeye.com/current-threats/threat-intelligence-reports.html espionage group. In the report, FireEye documented behavior patterns, techniques, tactics, software, indicator of compromises, exfiltrated data and the timeline of the attacks. MITRE ATT&CK framework simplifies these results to include a list of APTs with the techniques and tools that were found in the wild. As a supplement to the Cyber Kill Chain, the MITRE ATT&CK framework comprises a detailed list of tactics: Initial Access, Execution, Persistence, Privilege Escalation, Defense Evasion, Credential Access, Discovery, Lateral Movement, Collection, Exfiltration, Command and Control. Each of these tactics comprises a number of techniques which have grown over the years.
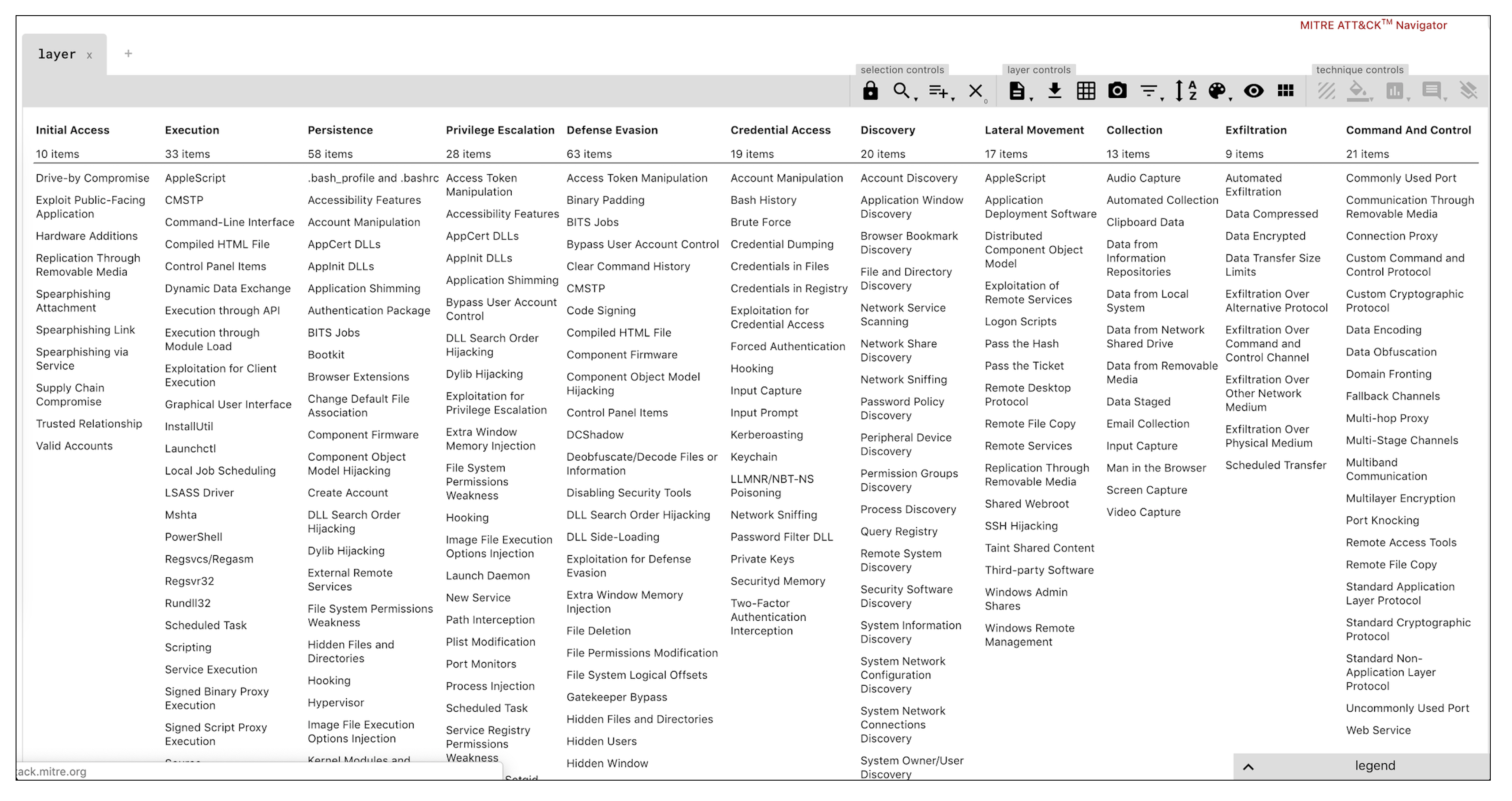
MITRE ATT&CK Framework (Zoom to read)
Threat Detection with UEBA & Anomaly Detection
Any deviation from what’s considered normal is an anomaly. For example, It would be anomalous if an organization’s employee accessed a sensitive file for the first time ever from a suspicious or completely new geolocation and deleted major chunks of data. That’s the kind of anomaly that can signal a major security breach—and that’s the kind of anomaly that must be prevented, detected in time, and remediated urgently.
Understanding UEBA & Anomaly Detection
UEBA or User and Entity Behavior Analytics analyzes various behavior patterns with large amounts of data within a sufficient time period to understand normal user behavior. It then uses the data collected to define baselines, to identify suspicious behavior, potential threats, and attacks that traditional methods may not detect. The key thing in UEBA is it identifies anomalous activities by looking at context information from a series of activities and establishing correlation between them. Warden Threat Detection analyzes logs from your infrastructure to perform UEBA to detect anomalies after learning the normal behavior of the users in the organization. It establishes a baseline for each organization or each user based on their previous activity patterns. It can detect any anomalous behavior when there are deviations from these “normal baseline” patterns. It can be due to a credential compromise, cryptojaking, or could be an early sign of insider threats.
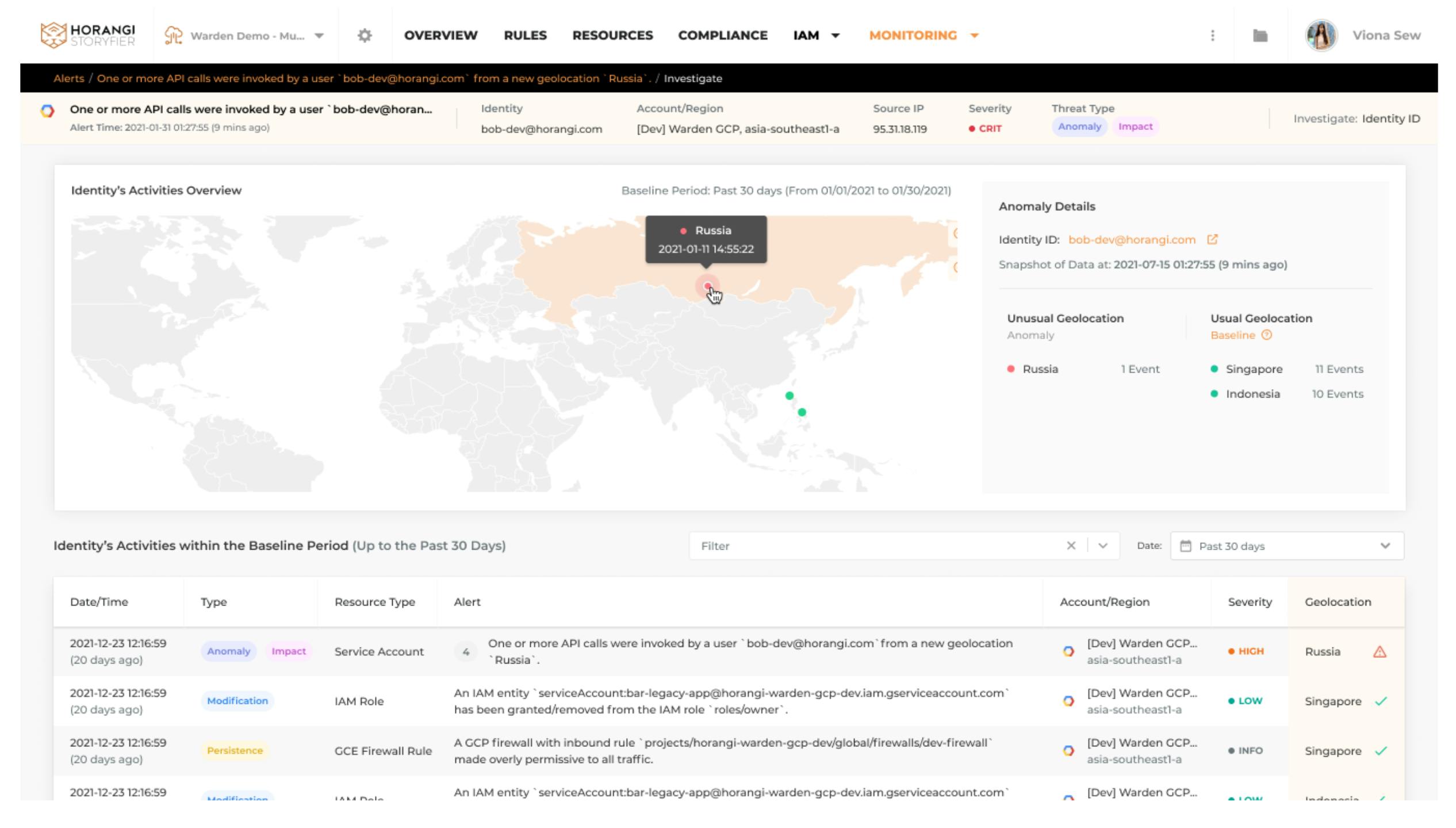
Here’s a video that you can watch to learn more about Threat Detection and how you can use a sophisticated tool like Warden to enforce the MITRE Framework for building your defense.
Conclusion
In today’s complex threat landscape, an attack is no longer a single malicious action or something that a single threat detector can help flag and protect your infrastructure. The attackers are using more advanced techniques and processes to get into your environment and it can only be flagged by looking at contextual information and using advanced cloud security tools. Warden Threat Detection continuously provides more effective and valuable detection use cases to enhance your company’s overall security posture. If you are curious to see this live in a 15 min demo, drop us a line here.




