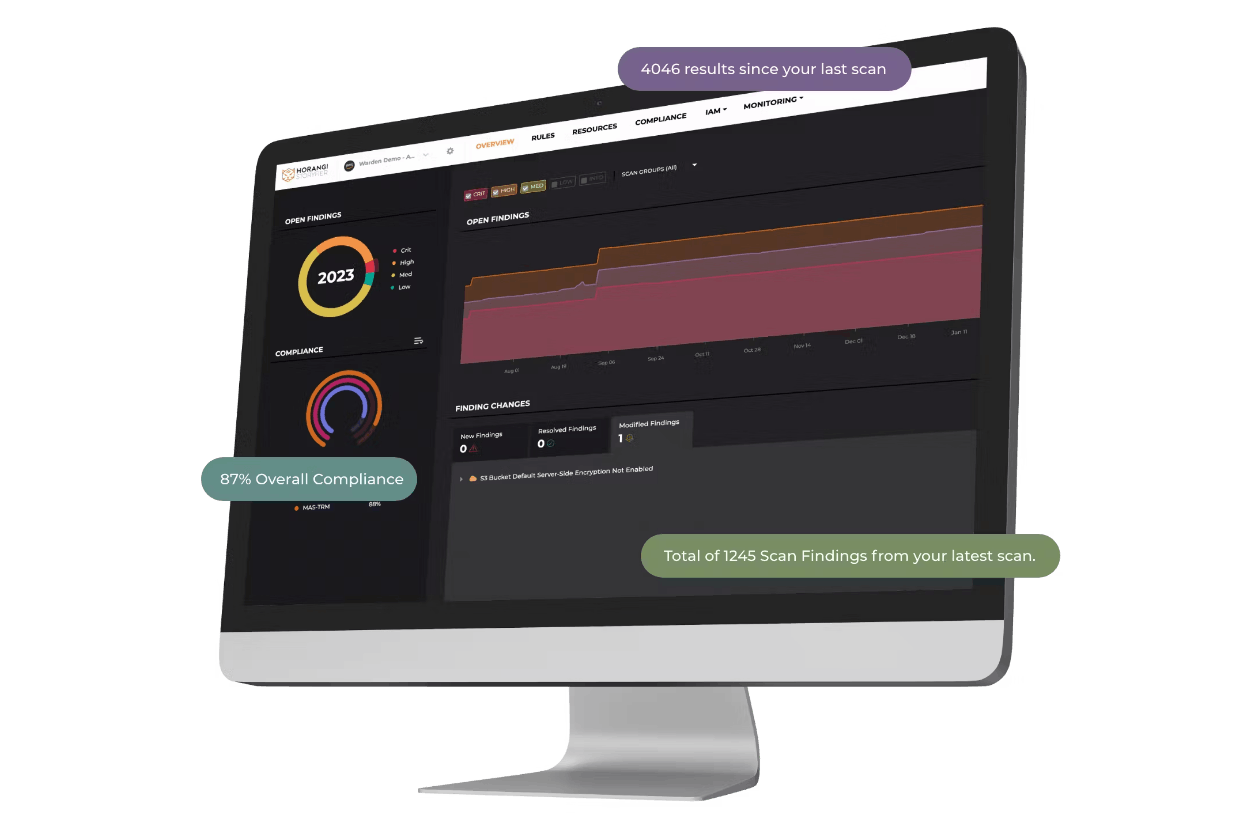
IAM Security
Limit the impact of a potential breach by 80% and tackle increasing complexity in managing infrastructure entitlements in a multi-cloud setup with Warden IAM.

IAM Security
Limit the impact of a potential breach by 80% and tackle increasing complexity in managing infrastructure entitlements in a multi-cloud setup with Warden IAM.
IAM Security
Limit the impact of a potential breach by 80% and tackle increasing complexity in managing infrastructure entitlements in a multi-cloud setup with Warden IAM.
IAM Security
Limit the impact of a potential breach by 80% and tackle increasing complexity in managing infrastructure entitlements in a multi-cloud setup with Warden IAM.

Threat Detection
Reduce mean time to investigate threats across your infrastructure with a detailed activity record on a unified dashboard.

Threat Detection
Reduce mean time to investigate threats across your infrastructure with a detailed activity record on a unified dashboard.
Threat Detection
Reduce mean time to investigate threats across your infrastructure with a detailed activity record on a unified dashboard.
Threat Detection
Reduce mean time to investigate threats across your infrastructure with a detailed activity record on a unified dashboard.

Vulnerability Remediation
Manage misconfiguration of resources and excessive permissions, with One-Click, Auto and Terraform remediation.

Vulnerability Remediation
Manage misconfiguration of resources and excessive permissions, with One-Click, Auto and Terraform remediation.
Vulnerability Remediation
Manage misconfiguration of resources and excessive permissions, with One-Click, Auto and Terraform remediation.
Vulnerability Remediation
Manage misconfiguration of resources and excessive permissions, with One-Click, Auto and Terraform remediation.

Compliance Automation
Automate compliance to always be audit-ready against popular frameworks such as GDPR, MAS TRM, APRA, SOC 2, OJK, and more.

Compliance Automation
Automate compliance to always be audit-ready against popular frameworks such as GDPR, MAS TRM, APRA, SOC 2, OJK, and more.
Compliance Automation
Automate compliance to always be audit-ready against popular frameworks such as GDPR, MAS TRM, APRA, SOC 2, OJK, and more.
Compliance Automation
Automate compliance to always be audit-ready against popular frameworks such as GDPR, MAS TRM, APRA, SOC 2, OJK, and more.

Posture Management
Harness the power of an all-in-one multi-cloud security tool with a unified platform for CSPM, CIEM, Threat Detection, and Vulnerability Management.

Posture Management
Harness the power of an all-in-one multi-cloud security tool with a unified platform for CSPM, CIEM, Threat Detection, and Vulnerability Management.
Posture Management
Harness the power of an all-in-one multi-cloud security tool with a unified platform for CSPM, CIEM, Threat Detection, and Vulnerability Management.
Posture Management
Harness the power of an all-in-one multi-cloud security tool with a unified platform for CSPM, CIEM, Threat Detection, and Vulnerability Management.

DevSecOps Integration
Integrate your existing workflows to get working fast. With third party channel integrations that include Slack, Github, Bitbucket, Jira, and any SIEM.

DevSecOps Integration
Integrate your existing workflows to get working fast. With third party channel integrations that include Slack, Github, Bitbucket, Jira, and any SIEM.
DevSecOps Integration
Integrate your existing workflows to get working fast. With third party channel integrations that include Slack, Github, Bitbucket, Jira, and any SIEM.
DevSecOps Integration
Integrate your existing workflows to get working fast. With third party channel integrations that include Slack, Github, Bitbucket, Jira, and any SIEM.
Click on each feature to read more about it.

Leading Managed Detection & Cybersecurity Consulting.
Leading Managed Detection & Cybersecurity Consulting.
Build cyber resilience for multi and hybrid cloud environments. Defend against advanced threats with CREST-accredited advisory and assessment services that keep you compliant with recognized frameworks such as NIST and ISO 27001.

Security and Risk Advisory
- CISO as a Service
- Cybersecurity Assessment
- Tabletop Exercise (TTX)

Security and Risk Advisory
- CISO as a Service
- Cybersecurity Assessment
- Tabletop Exercise (TTX)
Security and Risk Advisory
- CISO as a Service
- Cybersecurity Assessment
- Tabletop Exercise (TTX)
Security and Risk Advisory
- CISO as a Service
- Cybersecurity Assessment
- Tabletop Exercise (TTX)

VA, Penetration Testing, & Red Teaming
- Penetration Testing
- Red Teaming

VA, Penetration Testing, & Red Teaming
- Penetration Testing
- Red Teaming
VA, Penetration Testing, & Red Teaming
- Penetration Testing
- Red Teaming
VA, Penetration Testing, & Red Teaming
- Penetration Testing
- Red Teaming

Regulatory Compliance
- ISO 27001 Compliance
- MAS TRM Compliance
- OJK Compliance

Regulatory Compliance
- ISO 27001 Compliance
- MAS TRM Compliance
- OJK Compliance
Regulatory Compliance
- ISO 27001 Compliance
- MAS TRM Compliance
- OJK Compliance
Regulatory Compliance
- ISO 27001 Compliance
- MAS TRM Compliance
- OJK Compliance

Managed Threat Hunting
Threat Hunting
Compromise Assessment

Managed Threat Hunting
Threat Hunting
Compromise Assessment
Managed Threat Hunting
Threat Hunting
Compromise Assessment
Managed Threat Hunting
Threat Hunting
Compromise Assessment

Blockchain & Cloud Security
- Smart Contract Audit
- Source Code Review
- Cloud Security Assessment
- Security Architecture Review

Blockchain & Cloud Security
- Smart Contract Audit
- Source Code Review
- Cloud Security Assessment
- Security Architecture Review
Blockchain & Cloud Security
- Smart Contract Audit
- Source Code Review
- Cloud Security Assessment
- Security Architecture Review
Blockchain & Cloud Security
- Smart Contract Audit
- Source Code Review
- Cloud Security Assessment
- Security Architecture Review

Ransomware & Phishing Defense
- Ransomware Defense Assessment
- Phishing Simulations

Ransomware & Phishing Defense
- Ransomware Defense Assessment
- Phishing Simulations
Ransomware & Phishing Defense
- Ransomware Defense Assessment
- Phishing Simulations
Ransomware & Phishing Defense
- Ransomware Defense Assessment
- Phishing Simulations
Hear From Our Customers.

"My security alerts have reduced by 30% in just a few months of using Warden. This is an extremely powerful one-click tool that allows me to quantify how my organization's security posture is improving. The best part is that any user will be able to make full use of the platform, meaning you can start comprehensive cloud protection in minutes."
- Sashiraj Chandrasekaran, Engineering Team Lead, NalaGenetics
"My security alerts have reduced by 30% in just a few months of using Warden. This is an extremely powerful one-click tool that allows me to quantify how my organization's security posture is improving. The best part is that any user will be able to make full use of the platform, meaning you can start comprehensive cloud protection in minutes."
- Sashiraj Chandrasekaran, Engineering Team Lead, NalaGenetics

"It was a good experience - the response from Horangi was really fast and prior to the scope, the discussions were really crisp. The people who were part of the initial discussions were very knowledgeable, which gave us the confidence to be certain about working with Horangi for the long term."
- Narasimhan Partha, Group CTO, Direct Asia
"It was a good experience - the response from Horangi was really fast and prior to the scope, the discussions were really crisp. The people who were part of the initial discussions were very knowledgeable, which gave us the confidence to be certain about working with Horangi for the long term."
- Narasimhan Partha, Group CTO, Direct Asia