
Bitdefender Completes Acquisition of Horangi Cyber Security
Transaction Expands Bitdefender Product and Services Portfolio with Cloud Infrastructure Entitlement Management, Cloud Security Posture Management and Security Consulting Services

Bitdefender Completes Acquisition of Horangi Cyber Security
Transaction Expands Bitdefender Product and Services Portfolio with Cloud Infrastructure Entitlement Management, Cloud Security Posture Management and Security Consulting Services
Explore:
Featured List

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.
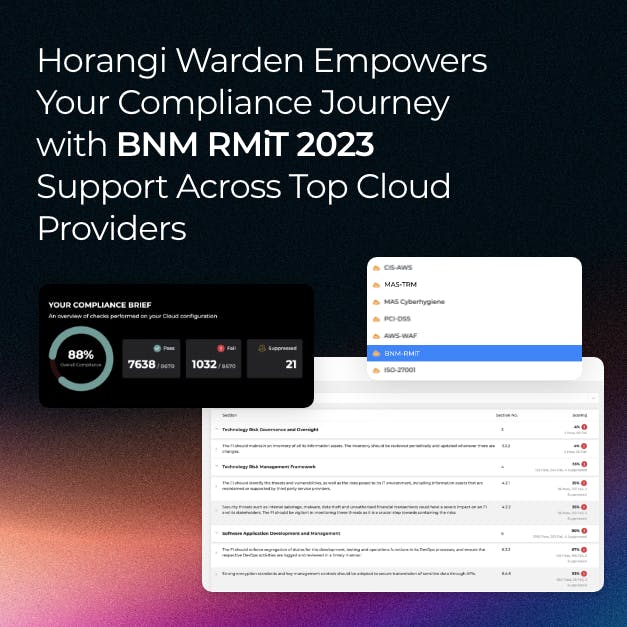
Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.
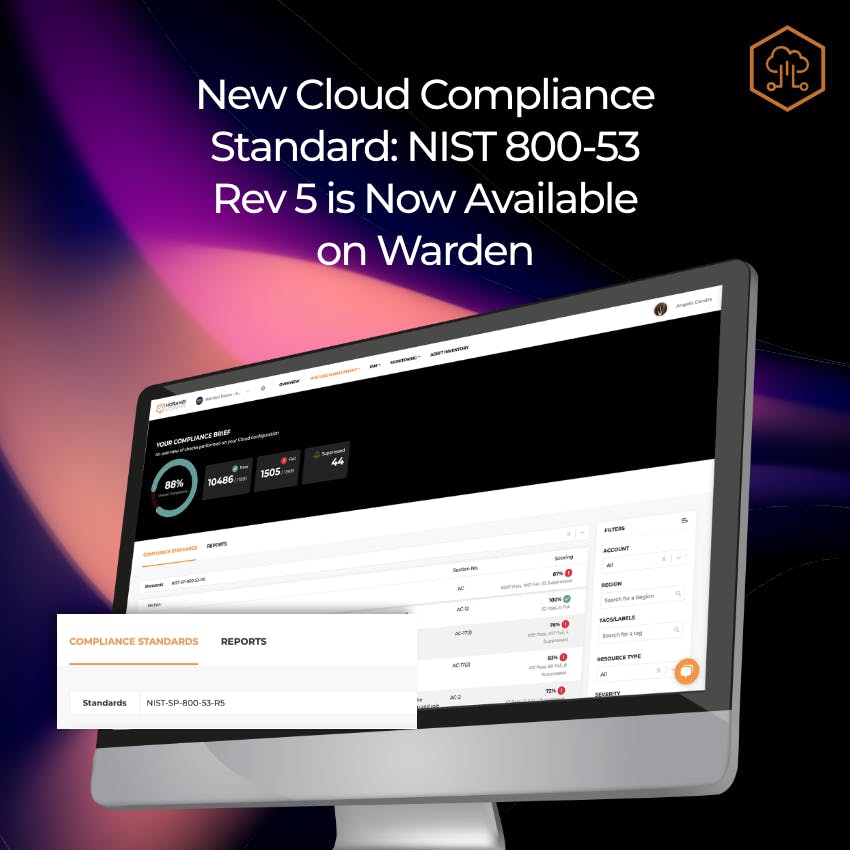
New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.
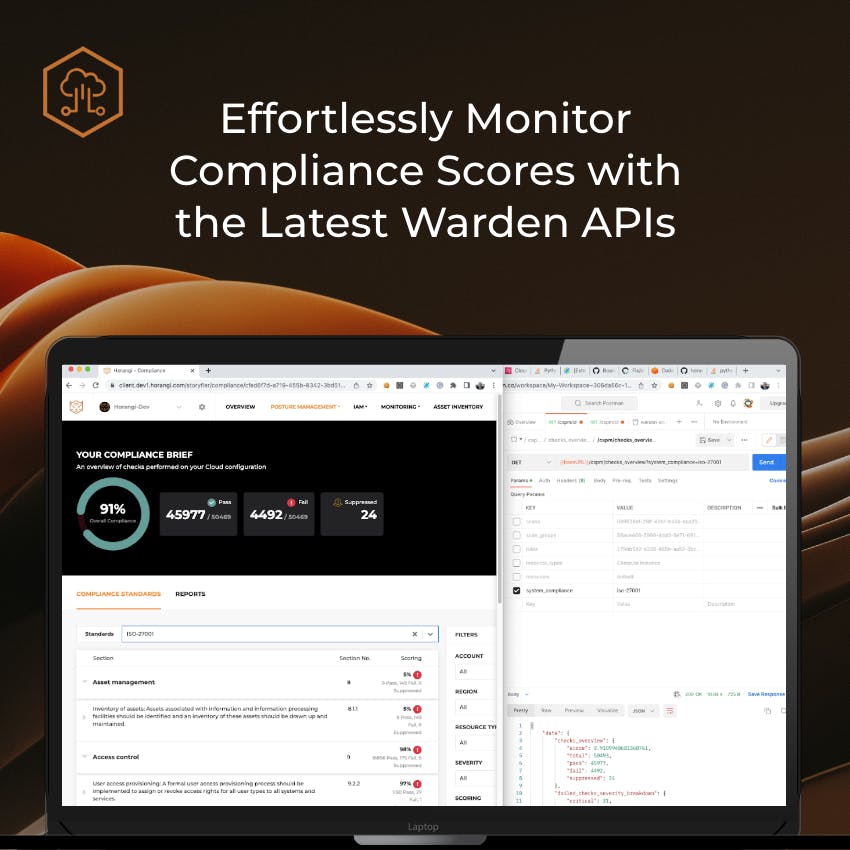
Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.
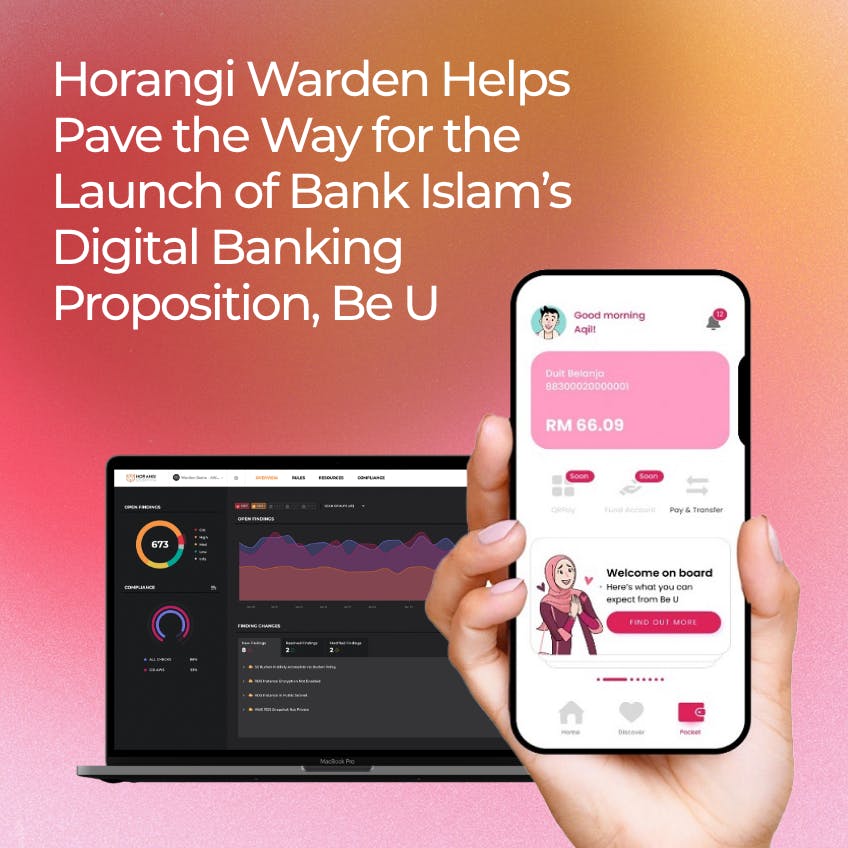
Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!
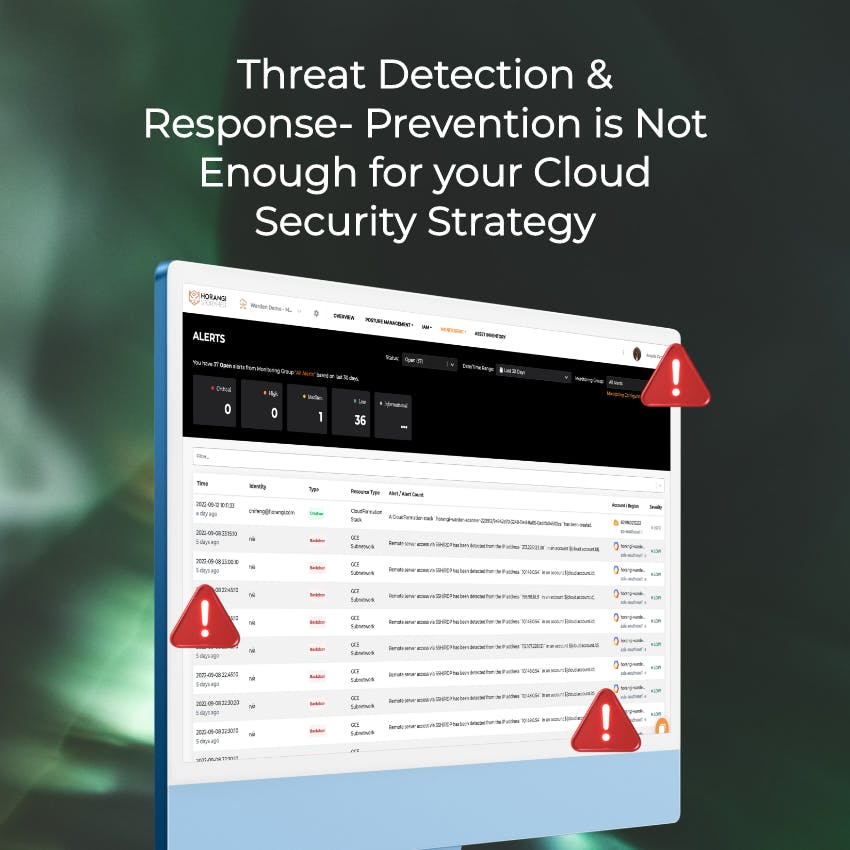
Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.
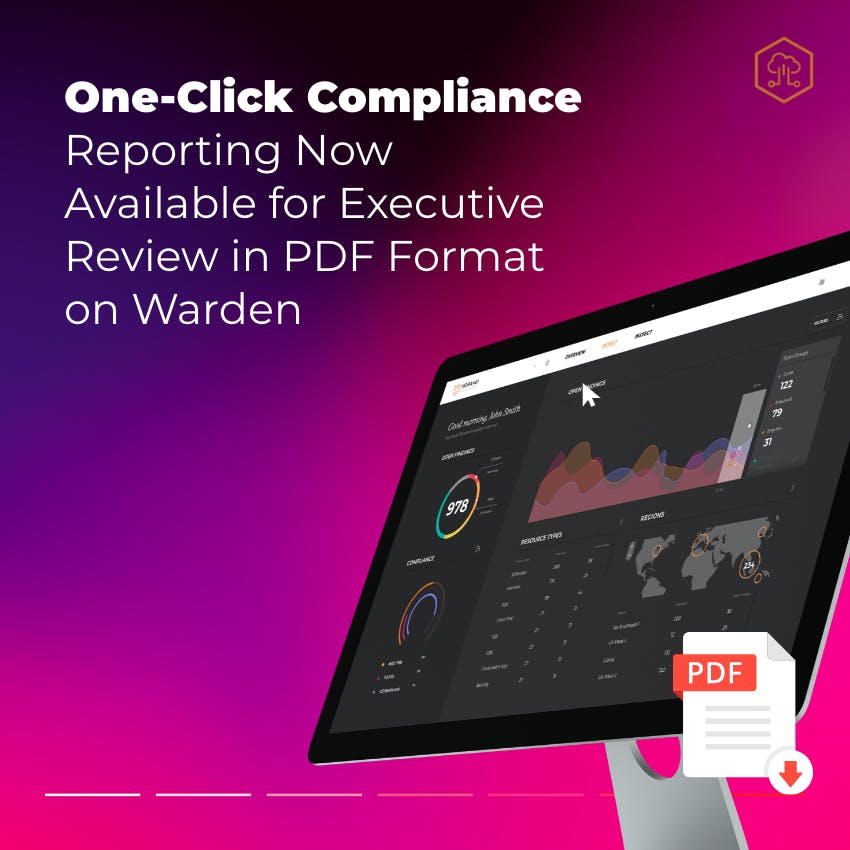
One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.
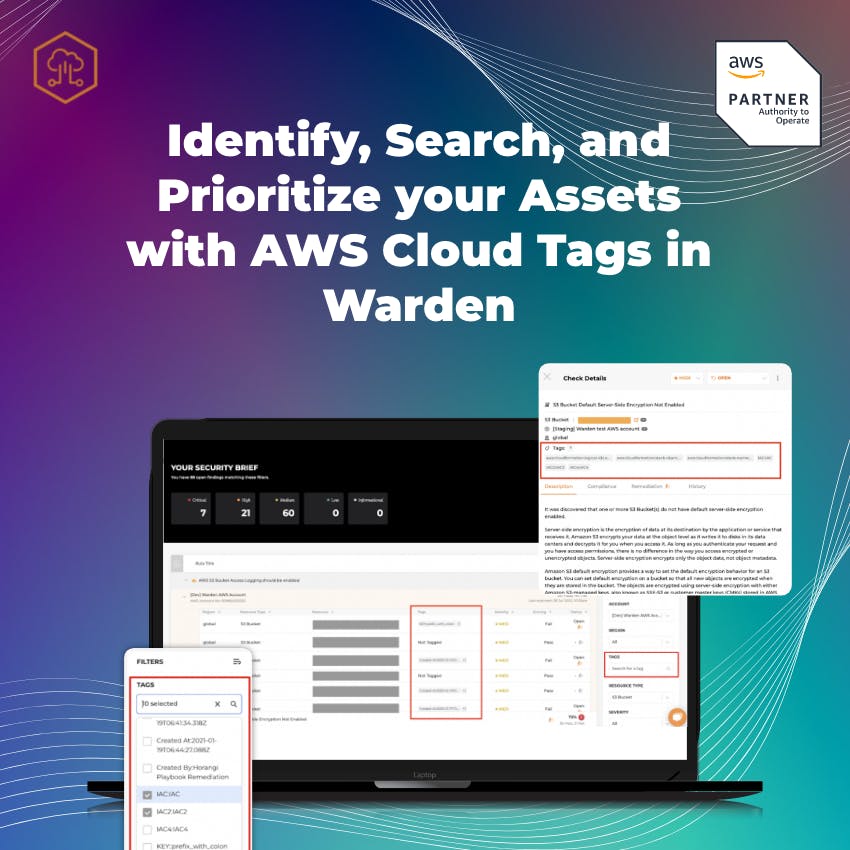
Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.
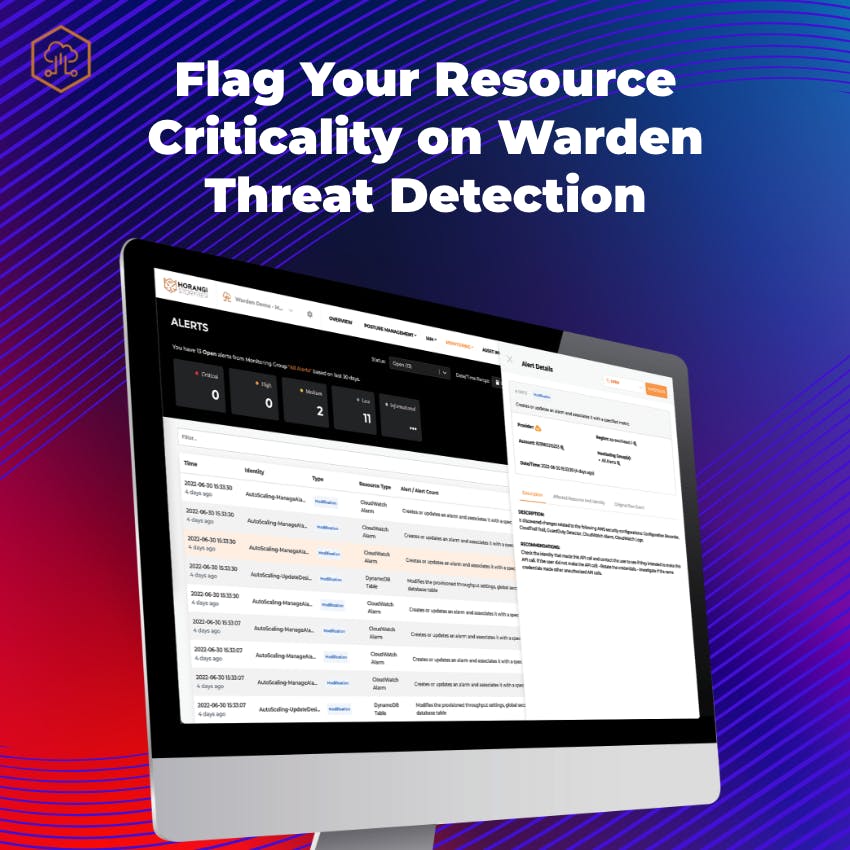
Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?
Explore:
Featured List
MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?


Bitdefender Completes Acquisition of Horangi Cyber Security
Transaction Expands Bitdefender Product and Services Portfolio with Cloud Infrastructure Entitlement Management, Cloud Security Posture Management and Security Consulting Services

Bitdefender Completes Acquisition of Horangi Cyber Security
Transaction Expands Bitdefender Product and Services Portfolio with Cloud Infrastructure Entitlement Management, Cloud Security Posture Management and Security Consulting Services
Explore:
Featured List

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?
Explore:
Featured List
MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

MOVEit Breach: The Largest Data Theft of 2023
This blog post dives into the MOVEit breach 2023, a significant cybersecurity incident impacting organizations and individuals globally. We explore the key factors contributing to the data breach, including the role of third-party risk management, incident response, and vulnerability and patch management, highlighting crucial lessons learned and strategies organizations can adopt to mitigate similar risks in the future.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Securing Your Mobile Application: The Importance of Mobile Application Penetration Test
The reliance on mobile applications, and how they are used everyday to handle our sensitive data and organisations premium services, necessitates a robust approach to security. In the below blog, it demonstrated that attackers exploiting vulnerabilities in mobile applications pose a significant threat to organisations. Read on to know how mobile application penetration testing emerges as a crucial proactive measure to simulate real-world attacks and uncover vulnerabilities.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cybersecurity Predictions 2024
As the digital era deepens, the ever-evolving landscape of cybersecurity demands a forward-looking perspective. Our aim is to provide a holistic view that encompasses both the evolving nature of cybersecurity threats and the enduring challenges that require continued vigilance and innovation.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

Cyber Strategy: Important Now, More Than Ever
Cybersecurity has never been a simple proposition. Organizations that once approached cybersecurity in simplistic terms as this are paying high prices for those misconceptions. Now, more than ever, protecting your organization’s information requires strategic thinking on various dimensions. Organizations need innovative, strategic thinkers to light the way.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

5 Reasons Cyber Security Tabletop Exercises are Essential for Every Business
Regardless of your industry, cyber attacks are inevitable if you are not prepared. Whether you work in critical infrastructure, financial services, healthcare or any other field, it's crucial to understand that these threats can affect anyone. Being prepared is essential in safeguarding your organization against potential cyber incidents, because it's no longer a matter of ‘if’ it will happen but a matter of ‘when’ it will happen.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Warden Empowers Your Compliance Journey with BNM RMiT 2023 Support Across Top Cloud Providers
With seamless compatibility across leading cloud providers like AWS, Azure, GCP, Alibaba, and Huawei Cloud, Horangi Warden proudly introduces support for the Bank Negara Malaysia Risk Management in Technology (BNM RMiT) 2023 standard. Read on to know how it can be the key to conquering security and compliance challenges.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

Horangi Cyber Security joins forces with Bitdefender!
Horangi Cyber Security to be acquired by Bitdefender, a global cybersecurity leader.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

CSPM, DevSecOps, and PoLP: How Warden Supports the Three Pillars of Cloud Security
Cloud security relies on three essential pillars: CSPM (Cloud Security Posture Management), DevSecOps (Development Security Operations), and PoLP (Principle of Least Privilege). These pillars form a solid foundation for comprehensive cloud security, protecting infrastructure, data, and applications. Read on to know how Horangi's tool, Warden, ensures resilience against emerging threats in the dynamic cloud environment.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

Warden's Integration with AWS Inspector for Enhanced Cloud Security - Open Beta
This integration brings together the power of Warden and AWS Inspector, allowing users to consolidate their security findings in one place. With a unified view, organizations can streamline their security operations and prioritize actions by correlating context across different findings. Read on to know more.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

The Silent Crisis: Exploring the Depths of The Cybersecurity Talent Shortage
Unraveling the depths of the global cybersecurity talent shortage, this blog article explores its causes and implications and highlights how businesses can navigate this challenging landscape.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

CVE-2023-22626 Error Based SQL Injection on PGHero
I was able to find two CVEs in a short period of time during a project I am working on last year. In this article, I will detail one of the vulnerabilities I discovered within PgHero.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

Do Business Leaders Truly Have No Concern for Cybersecurity?
This blog post will examine the role of business leaders in managing cybersecurity risks, the state of cybersecurity in businesses, the impact of cybersecurity breaches on businesses, the mindset of business leaders towards cybersecurity, and how to effectively communicate with business leaders.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

New Cloud Compliance Standard: NIST 800-53 Rev 5 is Now Available on Warden
Horangi, a cybersecurity company that offers cloud security services, has mapped their Warden CSPM rules to ensure that users can meet the compliance requirements of NIST 800-53 rev 5. Read on to learn more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Horangi Completes Smart Contract Audit for Hashport, Ensuring Security and Reliability
Smart contract audits are essential for minimizing the possibilities for attacker exploits. Horangi followed a rigorous methodology to deliver a detailed analysis of the smart contracts, an assessment of the risks, and a comprehensive report with recommendations for improvements to Hashport. Read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Simplify Cloud Resource Management with Google Cloud’s Label Support in Warden
Google Cloud Platform (GCP) labels are key-value pairs that allow users to manage and organize their cloud resources more effectively. This feature helps in keeping track of resources as cloud infrastructure grows by grouping resources together, tracking costs, managing access control, and streamlining operations. GCP labels support is now available on Warden - read on to know more.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

Exploring the Challenges of Application Security
In this episode, we talk about application security with guest Tanya Janca. Hear our discussion on the tension between authentication and authorization, the prevalence of API security flaws, the new OWASP API Security Top 10, and the inadequacy of API security measures.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

AI & ML in Cybersecurity
Join us on this episode of the Ask A CISO podcast as we discuss AI and ML in cybersecurity with Diana Kelley, CISO and co-founder of Cyberize. With International Women's Day in a week, we also looked at the challenges of recruiting women and diversity in the tech sphere.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

How to use IAM and UEBA to Secure Your Cloud
As you move more of your operations to the cloud, ensuring your cloud environment is secure becomes increasingly important. Two essential tools that can help with this are Identity and Access Management (IAM) and User and Entity Behavior Analytics (UEBA). In this blog, we'll explore using IAM and UEBA to secure your cloud environment and protect sensitive data from potential security threats.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

Indonesia's ‘Personal Data Protection Bill’ is Now Available on Horangi Warden in Bahasa
Indonesia's new law expands comprehensive protection of personal data to around 275 million individuals. The "Personal Data Protection Bill (Act No. 27 or 2022)" regulates the handling of personal data by public and private entities, including those outside Indonesia. This compliance framework is now available on Warden, offering mapping assistance to help organizations adhere to the Act's requirements and reducing the risk of non-compliance.

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

AI and the Future of Mobile Security
On this podcast's fourth episode, we learn about mobile security from Amit Modi, the Chief Technology Officer (CTO) and CISO of Movius Interactive Corporation, a leading global provider of cloud-based secure mobile communications software. We also chat about how mobile security will evolve with the advent of Artificial Intelligence (AI).

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Horangi Warden Mentioned as a CSPM Vendor in Gartner’s DevSecOps Report 2023
Gartner’s latest report ‘How to Select DevSecOps Tools for Secure Software Delivery’ talks about integrating developer-friendly security tools into your DevOps pipeline, where our product Warden is mentioned as a sample Cloud Security Posture Management (CSPM) tool.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

Effortlessly Monitor Compliance Scores with the Latest Warden APIs
The latest release of Warden introduces a powerful feature that allows you to effortlessly monitor compliance scores and find summaries using the Warden REST API. This feature unlocks numerous automated workflow possibilities and enhances your security orchestration, automation, and response solutions by reducing complexity and human error.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

4 Important Uses of CSPM and Real-Life Examples
Cloud computing has become a critical part of many businesses. However, the convenience of the cloud comes hand-in-hand with significant security risks that must be addressed to ensure data protection and compliance. In this blog, we look at four important uses of a CSPM that help your organization proactively manage and counter cloud security risks.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Cloud Compliance 101 [Infographic]
Compliance is never “one and done”. Given the highly dynamic, distributed nature of cloud environments and the fact that the rate of cloud deployments is only accelerating, cloud compliance can be exceedingly complex. Read on to learn about cloud compliance and and how automation can help you streamline auditing.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Unleash The Power of A CSPM Against Advanced Threats
So, you've migrated some of your company's operations and data onto the cloud and have procured or are thinking of getting a Cloud Security Posture Management (CSPM) tool to help secure it, but are you using it to the fullest? Have you wondered if there was more you could do with your CSPM? In this blog, let us help with some suggestions on how you can optimally use your CSPM to counter advanced threats.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Understanding DSPM & CSPM for Optimal Data Security
On this episode, we had the opportunity to speak to Tyler Young, the CISO at BigID, a leading modern data security vendor that helps organizations with their data security, privacy, compliance, and governance.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

Cybersecurity Risks and Business Context
After a brief hiatus, we are back with Season 3 of the Ask A CISO podcast. There are quite a few things we are doing differently this season (details below), but first, let's welcome our first guest for the new season: Fausto Lendeborg, Co-Founder and Chief Customer Officer of Secberus, and learn more about his start in cybersecurity, DDoS attacks, dealing with alert fatigue, and understanding what IaC, SaC, and PaC are.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

ChatGPT: A Boon Or Bane for Cybersecurity?
Unless you've been living under a rock, you'd indeed have read or heard of ChatGPT by now. Everyone's talking about how this new Artificial Intelligence (AI) bot can help in almost every aspect of life, from cooking recipes to providing code for a startup! What about cybersecurity? In this article, we look at what opportunities and threats ChatGPT presents in our field of work.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

What We Learned from the Biggest Data Breaches of 2022
Uber, Samsung, Twitter, Microsoft and more are among some of the biggest names affected in data breaches from last year. It goes to show that small or big, all organizations who use cyberinfrastructure can be at risk of a major security breach. Here are the key takeaways from the 10 biggest data breaches of 2022.

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Zero Trust 101 [Infographic]
The Zero Trust Security Model is not something that can be bought off-the-shelf, installed and implemented like many security products. It is a security framework based on a set of principles, which removes any implicit trust and enforces a “trust none, verify always” security model to safeguard your cloud infrastructure. Read on to understand the basics of Zero Trust and the Principle of Least Privilege (PoLP).

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Update your Findings with the New POST API Feature Added to Horangi Warden
With the release of this feature, you will be able to use Warden REST API not only to get data from our rich dataset, but also to post status/severity updates and add in remarks to security findings easily.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Asset Inventory as Your One-Stop-Shop for Your Cloud Assets Discovery & Review Now in Horangi Warden
Gaining visibility into resources and identities is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory has been improved recently to provide wider coverage, making it even easier and faster for your cloud security review.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Warden Threat Detection is Now Available on Alibaba Cloud
Time to respond is even more critical nowadays in the cloud as it can take just seconds for a hacker to infiltrate your infrastructure to steal large amounts of data, hijack cloud accounts, or set up compute-intensive operations like cryptomining without your knowledge. Warden can help you protect cloud infrastructure seamlessly and detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage, with around-the-clock monitoring. Horangi Warden Threat Detection is now available for Alibaba Cloud, for multi-cloud, real-time support.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Automate Your Workflow with Enhanced API Integration in Horangi Warden
With the release of this latest feature, Warden REST API gives you numerous ways to power up your own apps and integrations with our rich datasets! Read on to know how to streamline your cloud operations with the updated API integration with new ways to access and interact with Warden.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

Project Zero Trust
The old mantra that humans are the weakest link in cybersecurity should be discarded, according to George Finney. Listen in as we talk to him about why he thinks so, and why he drew from psychology, neuroscience, history, and economics for his first book Well Aware. We also had George define Zero Trust and talk about his new book Project Zero Trust, which includes a foreword from John Kindervag, the “father” of Zero Trust.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

New Compliance Standards including CCM, Korean ISMS-P, Thailand BOT, and more now Available on Horangi Warden
As your organization expands and grows, it is important to adhere to cybersecurity standards in different countries to stay compliant. We have added new cybersecurity control frameworks that will help you to define the processes and procedures that your organization must take to assess, monitor, and mitigate cybersecurity risk.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

How to Combat Alert Fatigue with Horangi Warden for Fastest Path to Compliance & Monitoring
Read on to learn great security insights and best practices from our product managers that can help bolster cloud security and threat management programs, while reducing your operating costs by 70%.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Modern Security Awareness Programs and People-Centric Cybersecurity
Cybersecurity awareness training can be long and boring. With shorter attention spans and work at the back of your mind, sitting through a training session may seem like a waste of time . How should cybersecurity awareness training be conducted in this landscape? We speak to Theo Nasser, Founder, and CEO of RIght-Hand Cybersecurity, to learn about modern cybersecurity awareness training and people-centric cybersecurity.

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Horangi Warden Helps Pave the Way for the Launch of Bank Islam’s Digital Banking Proposition, Be U
Anticipated as the cornerstone of all upcoming digital banks in Malaysia, Bank Islam launched Be U, a fully cloud-native digital banking application, on 18 July 2022, targeted at the digital-native, younger generation. Horangi, a leading cloud security solutions and services firm based in Singapore, was a significant part of that journey with Bank Islam by providing its flagship cloud security platform, Warden, for Be U’s launch. Read more below!

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

Threat Detection & Response: Prevention is Not Enough for your Cloud Security Strategy
It’s no secret that getting breached is a nightmare scenario, and it takes about 280 days for incident responders to detect and contain a breach, on average. Warden is enriched with intelligent threat detection for your multi-cloud environment, and continuously provides valuable detection use cases to enhance your company’s overall security posture.

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

One-Click Compliance Reporting Now Available for Executive Review in PDF Format on Warden
Suppose you frequently download Compliance Reports in Warden for review with your management, auditor, or other stakeholders. Horangi Warden’s new improvement will make this process faster and easier for you. This new feature will let you produce a well-designed compliance report in PDF format, without any reformatting or touch-up required. Read more below!

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

[Infographic] Cost of Attacks and Top Threats to Financial Institutions in 2022
Being prime targets for cyber attacks because of the high volume of personal information and financial assets, financial institutions experience more breaches while costs continue to rise. Securing your data on the cloud is vital to business and might save you from potential financial loss. Read on to know about top threats that can put your company’s assets at risk and best practices that can make a positive impact on your cloud security.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Threat Hunting and Incident Response
We speak to Harlan Carvey, Senior Incident Responder in R&D at Huntress, to understand what threat hunting is, and even learn how surprisingly easy it is to tell if an account has been compromised! Harlan and host Jeremy also explore the claim that there's a lack of cybersecurity talents, and whether organizations should have an organic incident response, outsource the function to managed service providers, or adopt an approach that combines both choices.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Ready, Game, Train, GO!
As an employer, it can be difficult to gauge the hands-on experience of potential cybersecurity hires. Yes, they come with the right degrees and the right certifications, but can they do what you are hiring them to do? How can you assess their hands-on capabilities? Eric Basu and his company, Haiku, Inc., created World of Haiku to help bridge the gap between employers and aspiring cybersecurity professionals. We talk to him this week to learn how the game came about, the difference between gamified training and games that train, and future plans for the game.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Your browser's local storage can be misused. Here’s what you should know.
Are you aware that your favorite websites actually store information in your browser? Find out what information is stored and see how that can be misused in this blog.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Identify, Search, and Prioritize your Assets with AWS Cloud Tags in Warden
As your cloud assets grow in size, it is vital to manage them with a systematic identification process - which is why a lot of organizations have an asset tagging strategy in place to keep important resources in check. Warden now lets users identify, search and filter with cloud tags so that you can manage your assets in Warden more efficiently. Read more below.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

Cyber Mayday And The Day After
Dan Lohrmann, award-winning CISO, keynote speaker, mentor, columnist, and bestselling co-author of the book Cyber Mayday and the Day After joins us this week to talk about cybersecurity roles in the public and private sectors, checklists for dealing with disruptions to your business, what organizations can learn from breaches, and much more including a lesson from a blackout on how tabletop exercises should be conducted.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

A Second Consecutive Win for Horangi Warden as a CIEM Vendor in Gartner’s Emerging Technology Report 2022
Horangi is a CREST-accredited SaaS company based in Singapore. With our product Warden, a multi-cloud security solution, Horangi has been listed as a Sample Vendor in the Emerging Technologies & Trends Impact on Products and Services published by Gartner in July 2022.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

Flag Your Resource Criticality with Better Contextual Insights on Warden Threat Detection
Never lose sight of your most important assets in the infrastructure with this exciting new update in Warden Threat Detection. You can now flag and segregate assets based on their criticality from the most critical to high, medium, and low priority. You can also get contextual alerts to identify and prioritize 24/7 monitoring, fixing them first before the attackers have a chance to compromise any of your critical assets. Read more below on how to get started with this.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

4 Important Reasons Why Your Organization Needs Threat Detection
Many talk about the importance of complete threat prevention, but ultimately, there is always a need for threat detection in all areas of your organization, whether it is over your endpoints or IT infrastructure. Read this article to find out the top reasons why.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Horangi Warden Named a Leader in G2 Summer 2022 Grid Reports in Cloud Security
Horangi Warden was built with a vision to make cloud security achievable with ease and help organizations of any scale and size to innovate without fear. With a customer-centric approach at its core, Warden’s team has been working tirelessly to build and constantly improve the product and cater to all their customers' use cases. And this G2 mention in the summer report 2022 as a ‘Leader’ in the Cloud Security category, is a testament to all the hard work that Horangi has been putting in. Read the full report here.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

Warden Threat Detection is Now Available on Huawei Cloud
It won’t be correct to say that you can stay 100% protected and never get breached. But we can say with certainty that we can help you protect cloud infrastructure seamlessly, with a 24/7 monitoring tool like Warden. Warden can help you detect threats in real-time, to quickly identify attacks or any suspicious activity and respond faster before it causes any damage. Read more below as we add another feather to our growing multi-cloud support with real-time threat detection recently released for Huawei Cloud.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

What Is PCI DSS 4.0 And How To Make Your Compliance Journey Easier?
Time is of the essence when you have just about two years to comply with the new PCI DSS 4.0 standard by 21 March 2024. Whether you are starting from scratch or updating your compliance from the current PCI DSS v3.2.1, read on to find out how your organization can use Warden's Compliance Automation to comply with PCI DSS v4.0 faster and with less pain.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

Custom Compliance Standard to Tailor-Fit Your Business Needs in Warden
We understand that every business has different compliance needs. With this feature, you don’t have to force a square peg into a round hole. You define the benchmark that matters to your organization, and let Warden monitor your cloud environment based on that custom standard. Read more below.

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

A CISO's Take On the Gartner Magic Quadrant
Many security leaders refer to Gartner's Magic Quadrant to decide on which security tool to purchase and deploy to secure their environments. The question then is whether it's good enough to just look at the quadrant the tool is in to guide your decision. What other factors should you consider?

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Demystifying CASB, CSPM, CWPP, and CNAPP For Your Organization's Cloud Security
The significant shift in adoption of cloud computing and the related risks that this is introducing is driving increasing interest toward controls that specialize on the unique cloud-based requirements. In this article we help you understand about these acronyms in detail and what each of them have to offer. Read more about CASB, CSPM, CWPP, and CNAPP below.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Warden IAM Asset Inventory to Discover & Flag Critical Resources in a Single Click
Gaining visibility into resources and policies is essential for a robust Cloud Security strategy. Read more on how Warden IAM Asset Inventory provides one place to easily see an aggregated view- to monitor and analyze and understand all assets across your multi-cloud setup.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Threat Detection for Dummies
Getting breached is a nightmare, and organizations that prioritize cloud security put smart people and tools to work 24/7 as a defensive barrier against malicious attackers. But security is an ongoing process—not a guarantee. What can you do then? You can build your knowledge base and your security arsenal with the right tools and an effective strategy for threat detection and response. Learn more below.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Top 5 Qualities For Succeeding In Tomorrow's Cybersecurity Industry
Surprise, surprise! A passion for cybersecurity is not even on the list of top 5 qualities for success in tomorrow's cybersecurity industry. Find out what employers are actually looking for today from Emil Tan, COO at Red Alpha and Founder of Infosec In The City.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

Get Notified of All Priority Alerts with AWS SNS Integration on Warden
Your security team might be using multiple channels to communicate and flag findings that your cloud security tool, a CSPM like Warden, alerts them about. This can lead to alert fatigue, and your team might feel lost in a pool of distributed notifications. Read more below on how you can consolidate these findings to increase your team’s efficiency.

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?

How Startups Can Overcome Limitations To Secure Their Business
Startups cannot afford to make the mistake of thinking of cybersecurity as an afterthought. Having a healthy, business-enabling cybersecurity posture from day one can be a daunting task given the limited budgetary and manpower resources, but not an impossible goal. How, then, can startups achieve that?


Subscribe to the Horangi Newsletter.
Be the first to hear about Horangi's upcoming webinars and events, up-and-coming cyber threats, new solutions, and the future of cybersecurity from our tech experts.

