What is Least Privilege Access?
The principle of least privilege refers to a crucial security concept in which a user (identity) is given the minimum levels of access (permissions/entitlements) needed to perform their job function. The principle of least privilege is a cybersecurity best practice and is a fundamental step in protecting access to high-value data and assets.
What Least Privilege does, in a nutshell, is limit the impact of stolen access credentials. If a malicious actor has stolen access credentials from one of your employees, for example, they will only have the minimum level of access needed by that employee to do their job. To use an analogy in the physical world: Least Privilege means that a thief who has stolen the keys of a bank’s receptionist won’t be able to enter the bank vault or the CCTV storage room. Since receptionists don’t need access to those places as part of their daily job, they shouldn’t have the keys to those places.
The Capital One data breach is a good example of what happens when the least privilege isn’t followed and things go wrong. In that famous 2019 data breach, an attacker managed to gain access to a Capital One server and then exfiltrate the personal data of 100 million customers because that server had access to sensitive cloud storage buckets that it didn’t require “in the normal course of business”.
Enforcing effective least privilege requires the right balance of security and convenience. Organizations will have to carefully guard privileged credentials and high-stakes data while enabling individuals with the freedom to innovate.
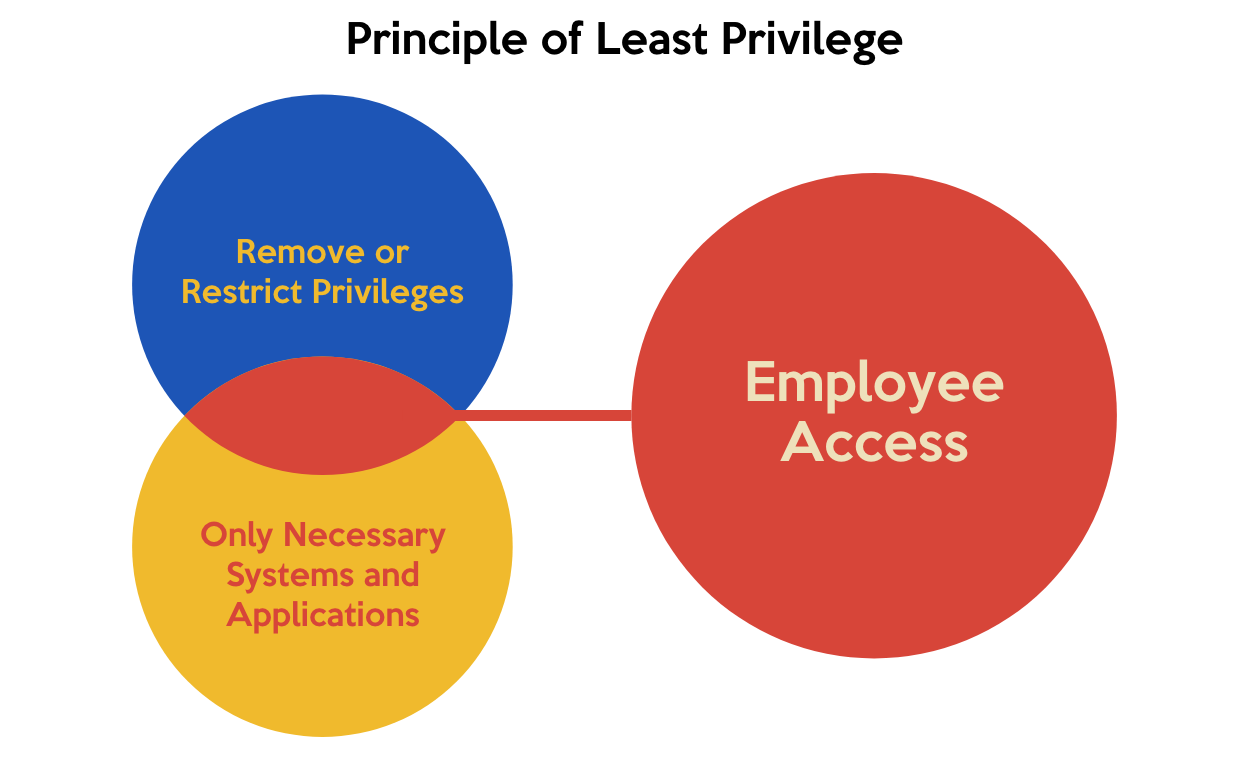
The Core of Principle of Least Privilege
Key Challenges
Scoping and managing privileged access remains a major challenge for most public cloud customers. Security Leads or DevOps Teams often enforce controls to manage and monitor privileged access, but this manual intervention process has many challenges.
- More than 65% of organizations allow unrestricted, unmonitored, and shared use of privileged accounts, which severely limits auditability and personal accountability
- In most organizations, developers, DBAs, and other system administrators are given full superuser rights, which is an egregious violation of the principle of least privilege
- Managing privileged access and shared accounts is cumbersome without specialized tools
- A lack of access governance for privileged accounts leads to the accumulation of excess privileges, orphaned accounts, ownership conflicts, and other governance issues
- Security solutions designed for on-premise systems aren’t well suited to tackle cloud IAM problems like the exponentially growing numbers of identities and cloud service permissions or the ephemeral nature of many cloud workloads
Finding Access Protection Solutions to Enforce Least Privilege
Maintaining the right level of access in an increasingly hybrid world is a big challenge, especially if you have cross-functional teams. Your internal staff requires access to applications both on-premise and in the cloud. And often, the tools used to manage access create operational inefficiencies for teams who have shared credential management responsibilities. Most organizations find a work-around to this problem, which unfortunately increases the chances of your credentials or sensitive information that can be compromised.
Gartner researchers frequently talk about the Continuous Adaptive Risk and Trust Assessment (CARTA) methodology as an effective way to solve this problem. CARTA can be considered as a multi-layer, defense-in-depth approach to protecting your infrastructure, and consists of tools and technology like Multi-Factor Authentication (MFA) and Identity and Access Management (IAM)Identity and Access Management (IAM) kits. These technologies help to define who gets access to what, when, and for what reason. Using these and other similar technologies can help mitigate the threat posed by user credentials being exploited.
Security tooling specifically designed for Cloud IAM SecuritySecurity tooling specifically designed for Cloud IAM Security
Cloud IAM security automation tools prevent cloud data breaches by automating the detection of identity and access management risks in public cloud environments including AWS, GCP, Azure, and Alibaba Cloud. They automatically discover all users and service identities and analyze their entitlements against their roles and policies, using a continuous lifecycle approach.
By combining analytics with granular, full-stack insights, IAM Security tools make it easy to understand who has access to what with which level of permissions, so that you can enforce least privilege access at scale even in the most complex cloud environments.
P.S. You can read more about IAM and the role it plays in protecting your crown jewels here.
Developing an Access Termination Policy for Least Privilege
Your organization should also focus on building and maintaining a specific set of policies for when employees leave their role or business unit. These rules should focus on security, so once a user no longer needs to have access, their entitlements should be removed for good from your infrastructure. Too often we see organizations forgetting to clean up stale, unused, or unnecessary permissions, which leads to considerable — and completely unnecessary — risk, as privileges, slowly balloon over time.
A typical Access Termination Policy often includes the following:
1. Why the employee is losing their access, listing out probable scenarios of why the access is being removed.
2. A standardized timeline or audit trail of the access removal process.
3. Guidelines surrounding the SLA of how third-party applications and websites will remove users from their platforms.
4. For high-stakes individuals who have access to extremely confidential data, you can also use a RACI chart (Responsible, Accountable, Consulted, and Informed) to define roles, responsibilities, and decision authority during the process.
Conclusion
To wrap up, how well your organization enforces the Principle of Least Privilege can act as a make-or-break factor when it comes to protecting your crown jewels from unwanted access. Security breaches can and will occur even in the most sophisticated of organizations. But with the least privilege access, the impact of a breach will be hugely reduced. Moving within your infrastructure to reach your sensitive systems will also require a lot more work.
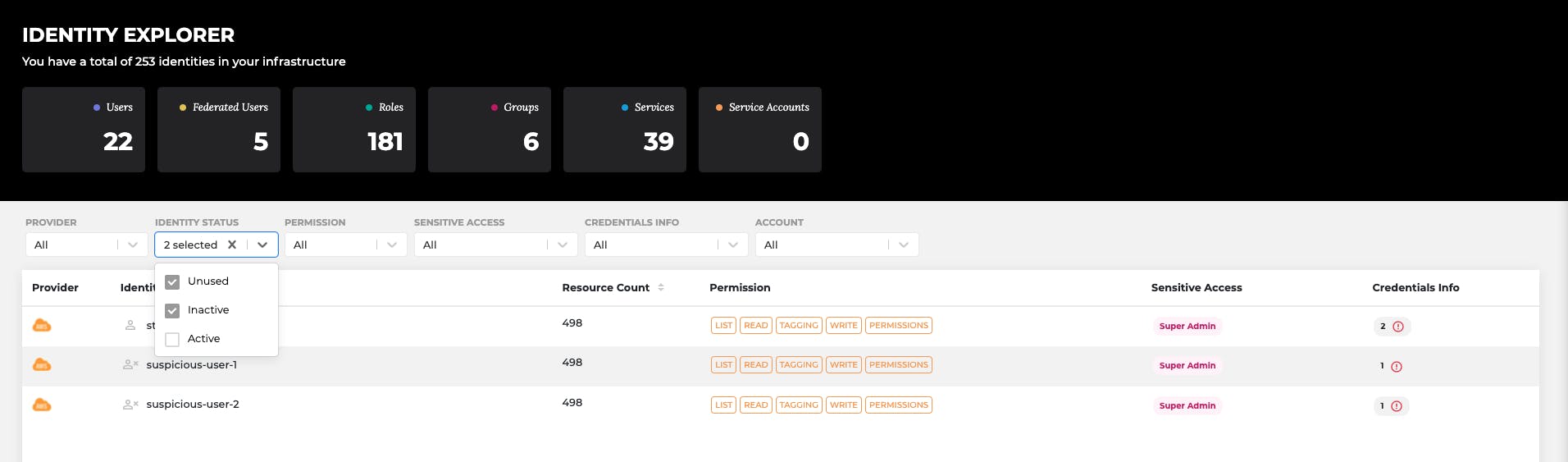
Warden IAM Identity Explorer Dashboard
While it sounds complex to enforce, this doesn’t need to be true. With the right, simple-to-use tools, you can make a big step towards Least Privilege within a short period of time. For example, with Warden IAM you can have visibility on who has access to what within minutes of setup (no coding involved). Once you have visibility of over-privileged users (see the image above) who shouldn’t have Read or Write permissions, you can easily remediate these to keep your infrastructure secure. To know more, fill this formfill this form and we will help you take Warden for a spin.




